I recently encountered a situation where I needed to demote a domain controller that was running on AWS. After the demotion had completed and the VM rebooted, I could not RDP back into the server. I don’t have a screenshot of the exact error message, but it was something along the lines of:
Connection to the server requires Network Level Authentication and no authenticating server could be found.

The server should have contacted another domain controller on the same network. Why it didn’t or couldn’t is a mystery for another day. Meanwhile, I had a dilemma on my hands. A pet peeve of mine with Windows VMs on cloud platforms is that RDP is essentially the only access method without a third-party solution. After trying various methods to resolve this, I found a solution that worked for me, which I’m eager to share.
The workaround involved using another server on the network to access the former domain controller via the remote registry, then modifying the registry to disable Network Level Authentication. Here are the details:
- RDP to another computer on the same network, preferably a Windows server.
- Install DNS services on it. Wait…what? Let me explain. This step was necessary because the domain controller I had demoted was also running DNS services, which I had removed as well. So, I needed to setup a temporary secondary DNS server.
If you’re not familiar with a secondary DNS server, it is a DNS server that has a read-only copy of records from a primary DNS server. It can handle DNS queries like a primary DNS, but it can’t modify any of the DNS records. The reason why I needed one will become clearer later. I will write a separate post on how to install and configure a secondary DNS server if you’re not familiar with the process.
- Wait or force the secondary DNS server to sync with a primary DNS server. Confirm it shows the record for the former domain controller.
- Open the Registry Editor and under the File menu click “Connect Network Registry…”
- Enter the name of the former domain controller. This is where the secondary DNS server comes into play. I couldn’t get remote registry to work initially because it couldn’t contact a DNS server. (Oddly enough, the secondary DNS could sync to a DNS server I have running in Azure, so why the remote registry couldn’t reach it is strange), but I digress.
- Once the remote registry is connected go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-TCP.
- Find the value “SecurityLayer”. When Network Level Authentication is enabled this value is set to “2”. Change it to “0” to disable it.
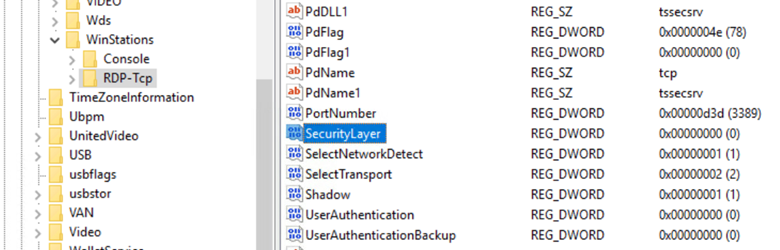
- The solution I found suggested to set “UserAuthentication” value to “0”. It was already set to “0” in my registry, so I can’t confirm whether this step is essential.
- Ok, let’s try RDP again to the former domain controller and…oh, snap same error as before. Doh, I need to reboot it. So, I initiated a reboot from the AWS EC2 console.
- Wait for about a minute, then try RDP again, and voila, I’m in!
I hope this helps anyone else that faces a similar situation. If you’ve run into this and have a better solution, please drop it in the comments below.





Leave a Reply